top of page
All Posts
Crown Equipment confirms cyberattack, disrupting manufacturing for several weeks
Crown Equipment Corporation, one of the largest forklift manufacturers in the world, employing 19,600 people and having 24 manufacturing plants in 14 locations worldwide, recently confirmed a significant cyberattack that disrupted its operations for weeks. The Attack and Immediate Response On June 9th, Crown Equipment’s network was breached by an international cybercriminal organization. The company’s […]
Jun 20, 2024
Cyberattack on CDK Global Affects Thousands of U.S. Car Dealerships
A recent cyberattack on CDK Global has caused a significant disruption in car dealerships across the United States. This cyber incident has brought thousands of car dealerships to a standstill, impacting their operations severely. Here is a detailed account of what transpired and the implications for the affected businesses. The Scope of the Attack CDK […]
Jun 19, 2024

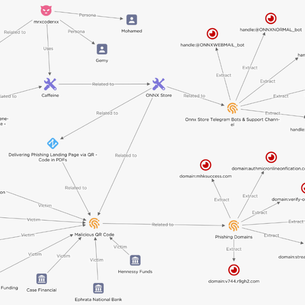
Phishing-as-a-Service Platform ONNX Store, Targets Financial Institutions and Microsoft 365 Accounts
In February 2024, EclecticIQ cybersecurity researchers discovered phishing campaigns targeting financial institutions using embedded QR codes in PDF attachments to redirect victims to phishing URLs. Recently, these campaigns have begun using a Phishing-as-a-Service (PhaaS) platform known as ONNX Store, which now targets both Microsoft 365 and Office 365 email accounts. The platform enables phishing attacks […]
Jun 18, 2024


Hackers Exploit High-Ranking Legitimate Websites to Deliver BadSpace Windows Backdoor
Overview of BadSpace Malware BadSpace is a sophisticated Windows backdoor malware that attackers deliver through compromised websites, especially those built on WordPress. This malware uses a multi-stage attack chain involving infected websites, command-and-control (C2) servers, fake browser updates, and a JScript downloader to infiltrate victims’ systems. Infection Chain: How BadSpace Infiltrates Systems According to German […]
Jun 17, 2024
Sophisticated Phishing Campaign Exploits Windows Search Protocol to Deliver Malware
A new, highly sophisticated phishing campaign has been detected by Trustwave that leverages HTML attachments to exploit the Windows search protocol, delivering malware through batch files hosted on remote servers. This article summarizes the mechanisms of the attack, mitigation measures, and insights into preventing such threats. Phishing Campaign Overview Researchers at Trustwave cybersecurity firm have […]
Jun 14, 2024
More_Eggs Malware Disguised as Resumes, Attacks Recruiters via Fake Job Applicant Phishing Scam
Cybersecurity researchers at eSentire have uncovered a sophisticated phishing attack leveraging the More_Eggs malware, disguised as job resumes. This tactic, identified over two years ago, continues to threaten organizations significantly. Recently, attackers targeted an unnamed company in the industrial services sector, underscoring the ongoing evolution of cyber threats and the need for heightened vigilance among […]
Jun 10, 2024


Advanced Surveillance Capabilities Discovered in macOS Variant of LightSpy Spyware
Cybersecurity researchers at ThreatFabric have uncovered a macOS variant of the LightSpy spyware, previously known for targeting iOS and Android devices. This development highlights the extensive reach and sophistication of this surveillance tool. LightSpy, a modular framework, has evolved to infiltrate various platforms, posing significant threats to user privacy and security. Origins and Evolution First reported […]
Jun 7, 2024


Terabytes of Advance Auto Parts’ Customer Private Data Compromised in Snowflake Attack
Advance Auto Parts, a major U.S. automotive aftermarket parts provider, has fallen victim to a significant data breach. Cybercriminals, operating under the handle “Sp1d3r,” claim to have stolen 3 terabytes of data from the company’s Snowflake cloud storage account. The stolen dataset, now being offered for sale at $1.5 million, includes vast amounts of sensitive […]
Jun 6, 2024
Rebranded Knight Ransomware Now Targeting Businesses Globally
RansomHub, a nascent yet prolific ransomware-as-a-service (RaaS) operation, has recently come into the limelight due to its rapid rise and significant impacts. Cybersecurity researchers have traced its origins back to the now-defunct Knight ransomware, itself a rebrand of the Cyclops ransomware. RansomHub has a short history and operated mainly as a data theft and extortion […]
Jun 5, 2024
Understanding the Threat Landscape: A Deep Dive into the Most Common Types of Cyber Attacks
In today’s interconnected digital world, cyber attacks have become an ever-present threat targeting individuals, businesses, and governments alike. Understanding the different types of cyber attacks is crucial for organizations and individuals to effectively mitigate risks and protect themselves against potential breaches. Here, we delve into 20 of the most common types of cyber attacks with […]
Jun 3, 2024
Okta Issues Warning on Credential Stuffing Attacks Targeting Cross-Origin Authentication Feature
Okta, a leading cybersecurity company specializing in identity and access management, has issued a warning about ongoing credential stuffing attacks targeting its Customer Identity Cloud (CIC) feature, particularly its cross-origin authentication. These attacks have been observed since April 15, 2024, affecting numerous customers. Credential stuffing is a type of cyber attack where threat actors use […]
May 30, 2024


Moonstone Sleet: The New Face of North Korean Cyber Threats
Microsoft has recently unveiled a new North Korean state-aligned threat actor named Moonstone Sleet, previously known as Storm-1789. This group is implicated in a series of sophisticated cyber attacks, blending traditional techniques with innovative methodologies to target various sectors, including software, IT, education, and defense. Moonstone Sleet’s operations highlight the evolving landscape of cyber threats […]
May 29, 2024
DNSBomb: A New, Practical, and Powerful Pulsing DoS Attack Exploiting DNS Queries and Responses
The digital landscape is rapidly evolving, bringing both unprecedented opportunities and new threats. Among the most concerning of these threats is the Distributed Denial of Service (DDoS) attack, particularly a novel variant known as DNSBomb discovered by researchers from the Tsinghua University in Beijing, China. This powerful and practical pulsing DoS attack exploits DNS queries […]
May 28, 2024
US Pharma Giant Cencora Data Breach Exposes Patient Information from 8 US Drug Companies
In February 2024, U.S. pharmaceutical giant Cencora, formerly known as AmerisourceBergen, suffered a significant cyberattack leading to a major data breach. The attack compromised the personal and highly sensitive medical information of individuals associated with eight prominent drug companies that partner with Cencora for pharmaceutical and business services. Details of the Data Breach The data […]
May 24, 2024


Sophisticated Crypto Mining Campaign ‘REF4578’ Deploys GhostEngine Malware
A malicious crypto mining campaign codenamed ‘REF4578,’ has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at the cybersecurity firms Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help […]
May 23, 2024


The Risks of AI-Powered Screenshotting: A Closer Look at Microsoft’s Recall Feature
With the rise of artificial intelligence, new features are continually being introduced to enhance user experience. The new Microsoft’s Recall feature, which captures screenshots of your active screen every few seconds and analyzes them using AI, exemplifies this trend by promising to enhance productivity with innovative AI-driven functionalities. However, despite its groundbreaking potential, this technology […]
May 22, 2024
CISA Issues Warning on Attacks Exploiting NextGen Healthcare Mirth Connect Flaw; Adds Vulnerability to Known Exploited Vulnerabilities Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently added a significant security flaw impacting NextGen Healthcare Mirth Connect to its Known Exploited Vulnerabilities (KEV) catalog. This action underscores the critical nature of the vulnerability, which has already seen active exploitation in the wild. The flaw, identified as CVE-2023-43208, has a serious impact due to […]
May 21, 2024
US Unveils Scheme Allowing North Korean IT Workers to Evade Sanctions
In a landmark case, The U.S. Department of State and U.S. Department of Justice have charged an Arizona woman, Christina Chapman, and an Ukranian man who, along with three unidentified foreign nationals, allegedly assisted North Korean IT workers in remotely working for US companies under false US identities. This scheme facilitated foreign IT workers in […]
May 20, 2024


WiFi Vulnerability Enables Eavesdropping Attacks Through Downgrade Strategy
A newly discovered vulnerability in the IEEE 802.11 WiFi standard, known as CVE-2023-52424, poses significant risks to network security. This flaw, dubbed the SSID Confusion attack, allows malicious actors to trick devices into connecting to less secure networks, thereby enabling eavesdropping type of attacks. The SSID Confusion Attack Researchers have identified a critical design flaw […]
May 17, 2024


Cybercriminals Exploit Windows Quick Assist for Ransomware Attacks
Cybercriminals have now identified a new vector for ransomware attacks by leveraging the Windows Quick Assist feature. Consequently, this emerging threat, primarily driven by a group known as Storm-1811, employs sophisticated social engineering techniques to deploy the notorious Black Basta ransomware. Therefore, understanding these tactics and implementing effective cybersecurity measures are crucial to mitigating these […]
May 16, 2024
bottom of page
